Topical Map for Cybersecurity Industries
Calvyn Lee Blog
JANUARY 5, 2024
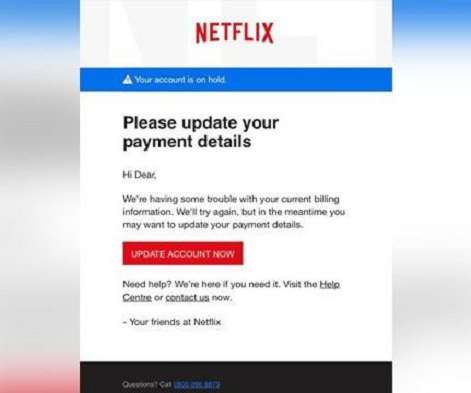
Define Your Niche: Clearly identify the main topics within the cybersecurity niche, such as “Network Security,” “Data Privacy,” “Cyber Threats,” etc. For instance, a page about “Firewalls” could have a URL like “/network-security/firewalls.”











































Let's personalize your content